In the fast-evolving realm of blockchain technology, security remains the paramount concern for developers and users alike. Polkadot, a sharded multichain network designed to enable interoperability and scalability for diverse blockchains, hinges its security on a sophisticated consensus algorithm. This article delves deep into the mechanisms of Polkadot’s consensus, examining each layer of its defense against possible vulnerabilities and threats, as well as its forward-looking approach to maintaining robust security measures.
Unveiling Polkadot’s Consensus
Polkadot’s consensus algorithm is a multi-faceted and intricate system designed to ensure the integrity of transactions and the finality of blocks across its network. At the heart lies the Nominated Proof-of-Stake (NPoS) system, which serves as the driving force behind the selection of validators and nominators. Here’s how Polkadot’s consensus unfolds:
- Validators are responsible for proposing and validating blocks.
- Nominators stake their tokens to select trustworthy validators.
- The algorithm ensures the best validators are chosen based on the amount of stake and reputation.
- Polkadot’s consensus utilizes the GRANDPA (GHOST-based Recursive Ancestor Deriving Prefix Agreement) mechanism to provide finality to blocks.
- BABE (Blind Assignment for Blockchain Extension) is used for block production through a verifiable random function.
- The two work in tandem to maintain both the liveliness and the irreversibility of the chain, positioning Polkadot as a state-of-the-art blockchain network.
Securing the Relay Chain

The Relay Chain is the central nerve system of Polkadot, connecting various parachains and managing their consensus and security. Protecting this core is paramount:
- Polkadot utilizes shared security, meaning the Relay Chain’s security is distributed across parachains.
- Validators and nominators’ stakes are on the line, creating an incentive to act honorably.
- Network “chill” periods can temporarily disable validators who misbehave.
- Multi-signature and threshold cryptography enhance the security of the validators’ activities.
- Decentralization of the Relay Chain is continuously improved to increase robustness against collusion.
- Activity on the Relay Chain is transparent, allowing for the community and specialized software to monitor for anomalies.
Validators & Nominators at Work
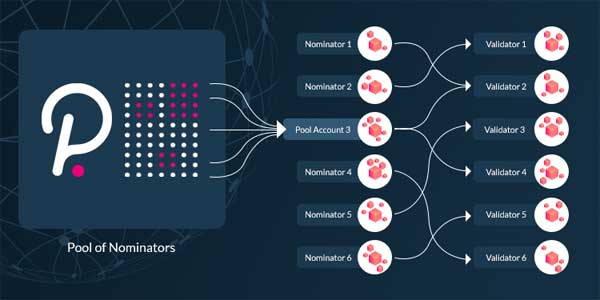
The actors of Polkadot’s consensus mechanism, namely validators and nominators, play a crucial role. Those acting as validators and nominators undertake responsibilities that are pivotal for network integrity:
- Validators run nodes to propose, validate, and finalize blocks, maintaining the security and consistency of the Relay Chain.
- Nominators back validators with their own stake, effectively increasing the stake of reliable validators.
- Quality of service is paramount; therefore, validators are strictly chosen based on their performance and the amount of stake behind them.
- A nominator can hedge risks by supporting multiple validators.
- Both stand to lose their stake as a penalty if a validator they support acts against the network’s rules (slashing).
- This strategic interaction between nominators and validators underlies the security and trust of the Polkadot network.
Resistance Against Attacks
Polkadot’s consensus design targets maximum resistance against a range of malevolent threats to uphold a secure environment:
- Sybil Attacks: Polkadot counters these by requiring validators to stake significant amounts of DOT, making the cost of the attack prohibitively expensive.
- Nothing-at-Stake Problem: Slashing mechanisms discourage validators from validating multiple blocks at the same layer.
- Long-Range Attacks: The consensus uses checkpoint finality to prevent rewriting of the chain far in the past.
- DDoS Attacks: Polkadot’s diversified node infrastructure and rotating validator assignments decrease the network’s susceptibility.
- Spread of validator nodes across geographies and host providers mitigates risks of localized disruptions.
Combined, these defenses shield the network, ensuring reliability and uninterrupted continuity of the Polkadot blockchain.
Polkadot’s Security Arsenal
A series of security measures fortify the Polkadot network beyond the consensus mechanism. Among these defensive layers are:
- An active community and council that govern and continuously update the security measures.
- Specific bug bounties and incentives for white hat hackers to report vulnerabilities.
- Integration with state-of-the-art cryptographic techniques to safeguard communications and operations.
- Thorough onboarding process for validators to assure only capable and secure nodes join the network.
- An adaptive and flexible governance model enabling procedural changes in response to detected threats.
- Cross-chain message passing (XCMP) ensuring safe interaction and data transfer between parachains.
Comparison of Polkadot’s Consensus Features to Other Blockchains
| Feature | Polkadot | Other Blockchains |
|---|---|---|
| Consensus Model | NPoS + GRANDPA/BABE | PoW, PoS, DPoS, etc. |
| Finality | Explicit with GRANDPA | Probabilistic |
| Block Production | Predictive (BABE) | Competitive (e.g., PoW) |
| Interoperability | Built-in (XCMP) | Varies (often limited) |
| Update Mechanism | On-chain governance | Off-chain coordination |
| Resistance Scale | High (Economic & Cryptographic) | Medium to High (Varies) |
Future-Proofing Consensus

Looking ahead, Polkadot is committed to not only maintaining but also advancing its consensus algorithm to meet evolving challenges:
- Research and development are ongoing for quantum-resistant cryptographic methods.
- The protocol’s flexibility allows for incorporating future insights in governance, cryptoeconomics, and algorithmic efficiency.
- Continued expansion of the validator pool and distribution promotes a more resilient network.
- Opportunities for community participation in consensus and security are ever-expanding.
- The economic model will be adjusted over time to align with the incentive structures of validators and nominators.
- Polkadot’s open-source ethos encourages collaboration across the industry to reinforce collective security knowledge.
In conclusion, Polkadot’s consensus algorithm is intricately designed to safeguard the network against various security threats, while remaining adaptable for future advancements. The interplay between validators, nominators, and the unique NPoS model, coupled with GRANDPA and BABE, forges a consensus mechanism that is both robust and sophisticated. Through constant vigilance and innovation, Polkadot exemplifies a forward-thinking blockchain, ready to adjust its sails in the uncharted waters of cybersecurity challenges.

The article mentions Polkadot’s bug bounties for white hat hackers. This is good for security.
Shared security and decentralized Relay Chain make Polkadot robust against attacks.
Polkadot’s use of XCMP for safe data transfer between parachains is interesting.
Polkadot uses NPoS for security. Validators and nominators play key roles.
The article explains Polkadot’s consensus well. Validators and nominators are important.
GRANDPA and BABE provide finality and block production. These help keep Polkadot secure.
Polkadot’s consensus includes measures against Sybil and DDoS attacks. It seems very secure.
Polkadot is preparing for future threats with quantum-resistant cryptography and flexible governance.